VST ECS Phils. Inc. joins the CyberArk Partner Network to expand its security solutions portfolio. CyberArk offers the most comprehensive Identity Security Platform to secure and protect human and machine identities.
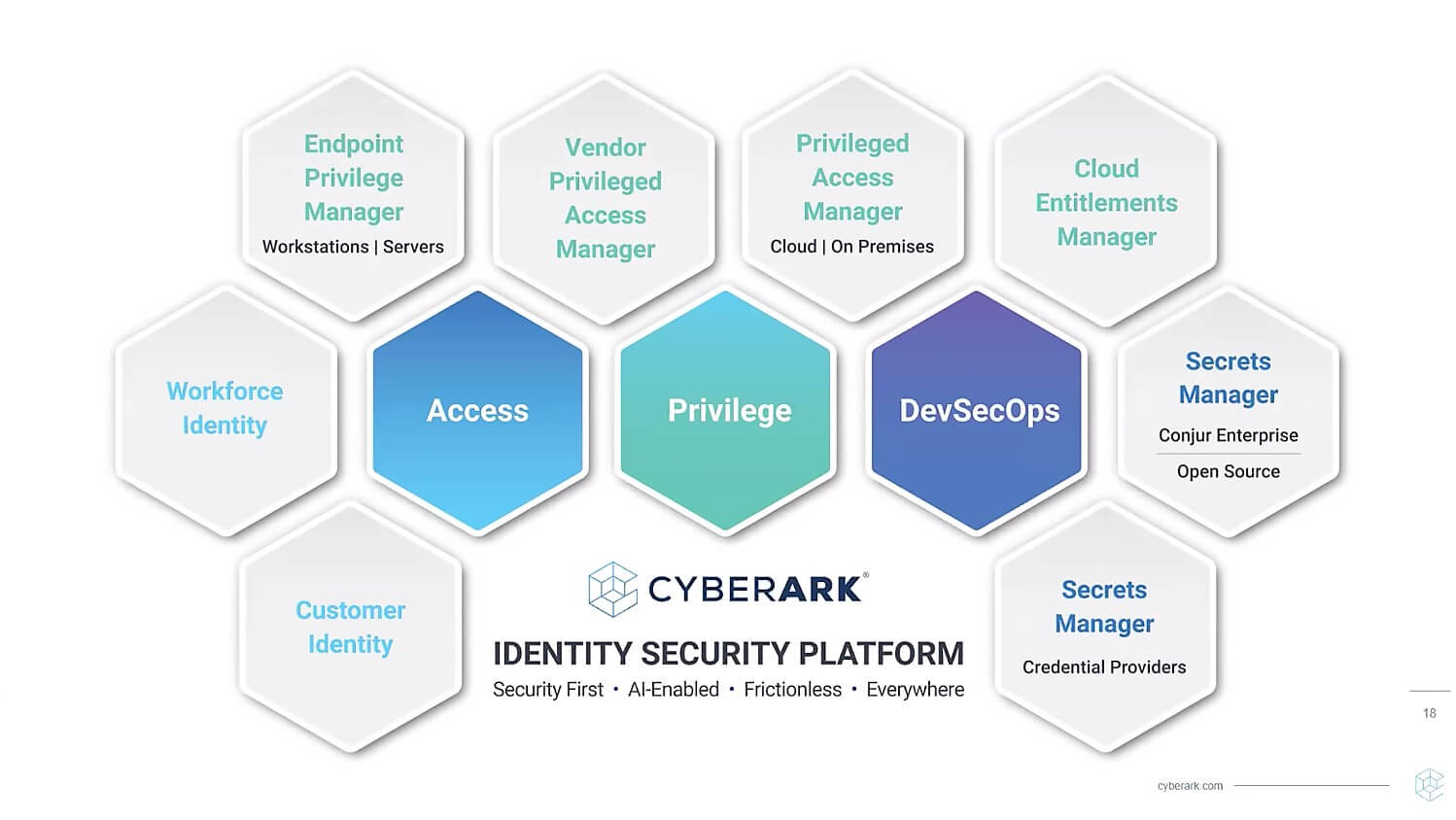
CyberArk, the global leader in identity security, provides the industry's most comprehensive Identity Security Platform for securing and protecting human and machine identities. The CyberArk Identity Security Platform, which is focused on privileged access management, enables clients to take a single and comprehensive approach to safeguarding access for any users, across any type of application or system, from any environment, and on any device.
“During the pandemic, businesses were forced to embrace digital technologies and increase online presence for continuity and resilience. However, as more devices access corporate networks from multiple locations and environments, organizations have become more vulnerable to security breaches and cyberattacks. This digital rush has increased possible attack surfaces and exposed vulnerabilities. Cybercriminals continue to innovate and are now using machine learning to infiltrate corporate networks. As threats continue to evolve, organizations need to rethink their security and risk strategies. Now that Identity Security is a major priority, our appointment as the country distributor of CyberArk comes at the right time. With CyberArk’s complete suite of identity security portfolios, organizations can be more confident to embrace digital transformation without compromising the security aspect of their businesses. There is a high demand now for identity security solutions, and I am confident that our partnership will bring more opportunities for our channel partners,” said Jimmy Go, president, and CEO, VSTECS Phils. Inc.
The solutions provided by CyberArk enable the following:
Secure Privileged Access
Industry researchers estimate that 80% of security breaches occur as a result of compromised privilege credentials. CyberArk allows you to isolate and stop privilege attacks before they do harm. Your users will have native access to everything they require, and you will have peace of mind knowing that your important assets are secure. CyberArk Privileged Access Management solutions protect privileged credentials and secrets wherever they reside: on-premises, in the cloud, or everywhere in between.
Access to Business Resources
The next struggle for security is identity. A robust passwordless experience provides users with easy access – while AI protects against attacks. Provide easy, secure access to your workforce and customers from any device, anywhere, and at the right time. CyberArk Workforce Identity and Customer Identity solutions analyze behavioral signals in real-time to ensure that your users are who they claim to be.
Secure DevOps
Innovative tools for application and automation are essential. The problem is that they are an often targeted victim of sophisticated cyberattacks. You can help assure security across the DevOps pipeline with CyberArk — without jeopardizing business agility. CyberArk Secrets Management solutions enable apps and automation tools to safely access sensitive resources at scale – without putting developers at a disadvantage. Security teams can collaborate with developers to create agile, safe, and productive supply chains and development environments with the correct tools and strategy.
To learn more about CyberArk, please visit www.cyberark.com or email Glenn Quiambao at gquiambao@msi-ecs.com.ph.
For more tech news and gadget reviews, please follow us on Facebook (facebook.com/Adobotech), YouTube (Adobotech TechBlog) and Twitter (@adobotech).

















No comments:
Post a Comment